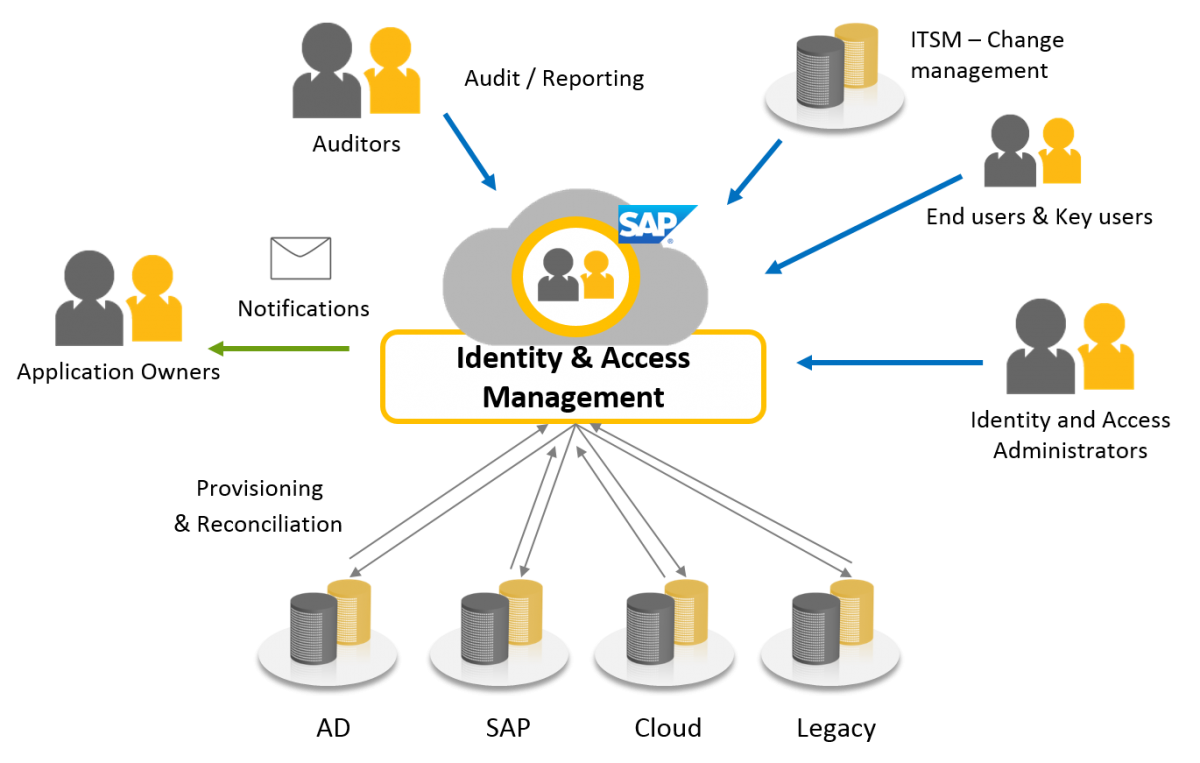
Identity and Access Management

Manage user identities
Identity and Access Management systems can be the sole directory used to create, modify, and delete users, or it may integrate with one or more other directories and synchronize with them. Identity and access management can also create new identities for users who need a specialized type of access to an organization's tools.
Provisioning and Deprovisioning Users
Specifying which tools and access levels (editor, viewer, administrator) to grant a user is called provisioning. Identify and Access Management tools allow IT departments to provision users by role, department, or other groupings in consultation with the managers of that department.
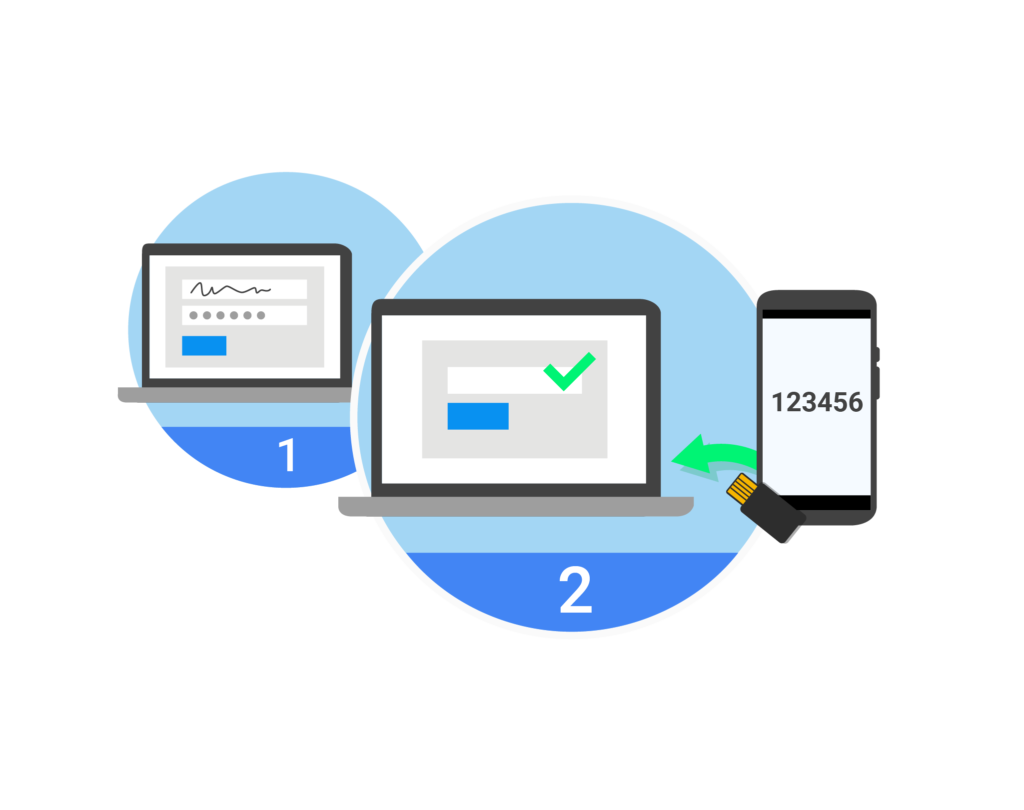
Multi-factor Authentication
Adds another layer of protection by requiring users to present two or more identifying credentials in addition to a username to gain access to applications.

Risk-based Authentication
Also known as adaptive authentication, a risk-based authentication solution prompts a user for Multi-factor Authentication only whenit detects the presence of higher risk.

Authorize Users
Access management ensures a user is granted the exact level and type of access to a tool that they're entitled to. Users can also be portioned into groups or roles so large cohorts of users can be granted the same privileges.

Reporting
Identity and Access Management tools generate reports after most actions taken on the platform (like login time, systems accessed, and type of authentication) to ensure compliance and assess security risks.
What they're saying






 IN
IN KN
KN ZA
ZA
